In today's digital landscape, businesses are increasingly migrating to the cloud to enhance efficiency and scalability. However, choosing the right cloud service provider is paramount […]
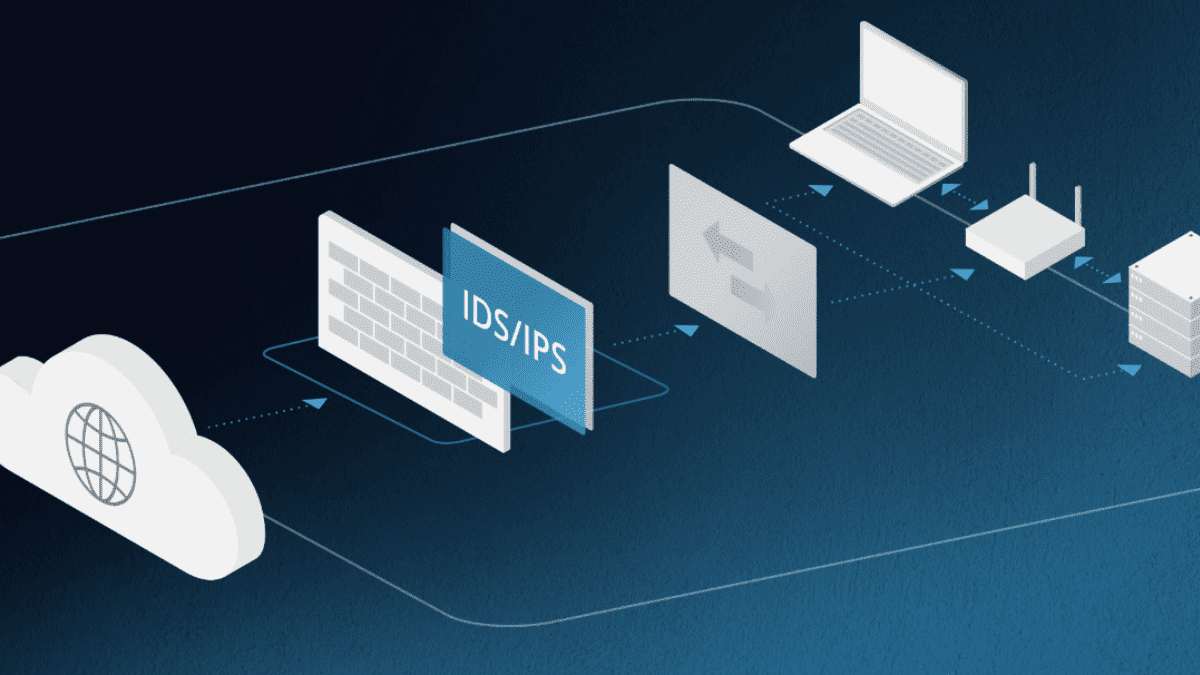
To effectively safeguard networks, businesses must choose the right IDS implementation based on their specific security needs. Below is an overview of the primary IDS […]

Breach recovery is a critical process that organizations must navigate after experiencing a security incident. Understanding its significance and the steps involved can help organizations […]
Cloud elasticity refers to the ability of a cloud computing environment to dynamically allocate and deallocate resources based on workload demands. This flexibility allows organizations […]

Securing a home network is critical for individuals and small to medium enterprises (SMEs) that rely on the internet for daily operations. A compromised network […]
In today's fast-paced business environment, efficient IT support is crucial for the success of small and medium-sized enterprises (SMEs). Implementing the best software solutions for […]
For businesses in Cincinnati, selecting the appropriate cloud services is crucial to stay competitive and meet specific operational needs. Choosing the right cloud services […]

More businesses in Cincinnati are shifting to cloud computing because it lowers costs, enhances security, and improves efficiency. Cloud-based solutions eliminate the need for expensive […]
Selecting the right cloud services provider is crucial for your business's efficiency and security. A suitable provider can enhance operations, while a mismatched choice may […]


