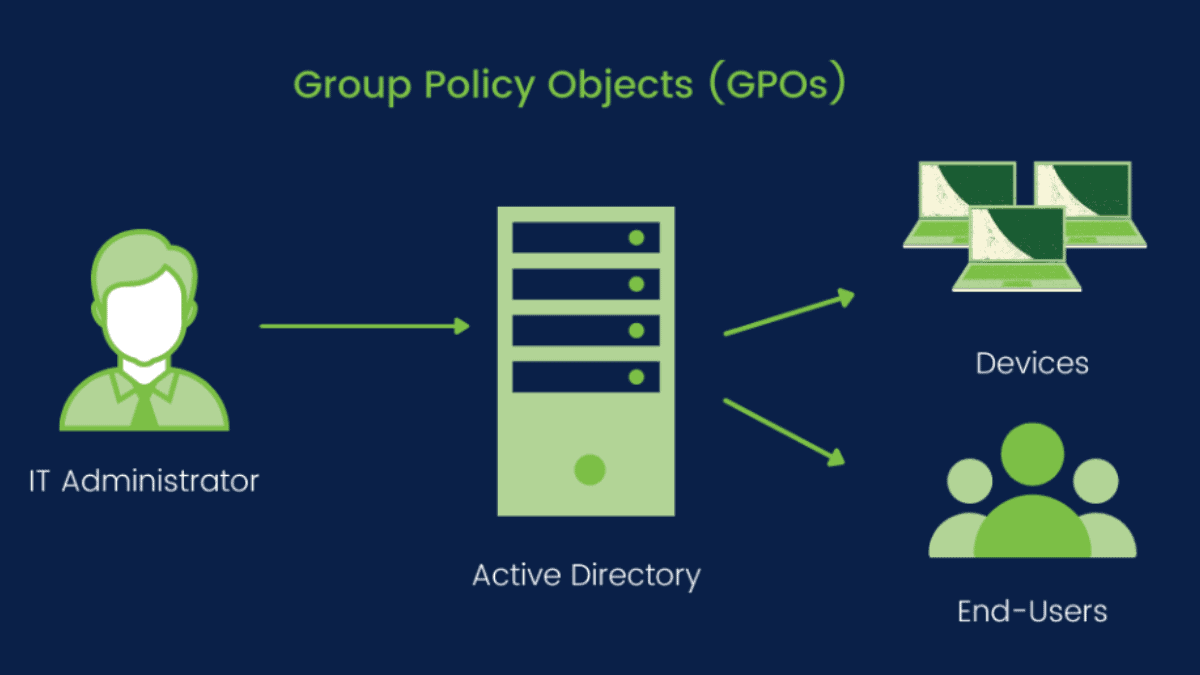
Group Policy is a critical feature within Windows networks that enables centralized management of operating system settings, applications, and user configurations. This tool allows IT […]

Roaming profiles are a feature used in IT systems that allow a user’s personal settings and files to follow them across multiple devices within a […]

Information technology defines a trust relationship as a connection between two entities, such as users, applications, or systems, allowing for the secure sharing of resources […]
Cybersecurity organizations employ strategies such as the Red Team vs. Blue Team approach to enhance their security posture. This method involves simulating cyber attacks to […]
Email links are often the entry point for cyber threats targeting businesses, particularly small and medium-sized enterprises (SMEs). Understanding the associated risks and tactics used […]

A Cloud Access Security Broker (CASB) acts as a vital mediator between users and cloud service providers. It provides visibility and control over cloud applications, […]
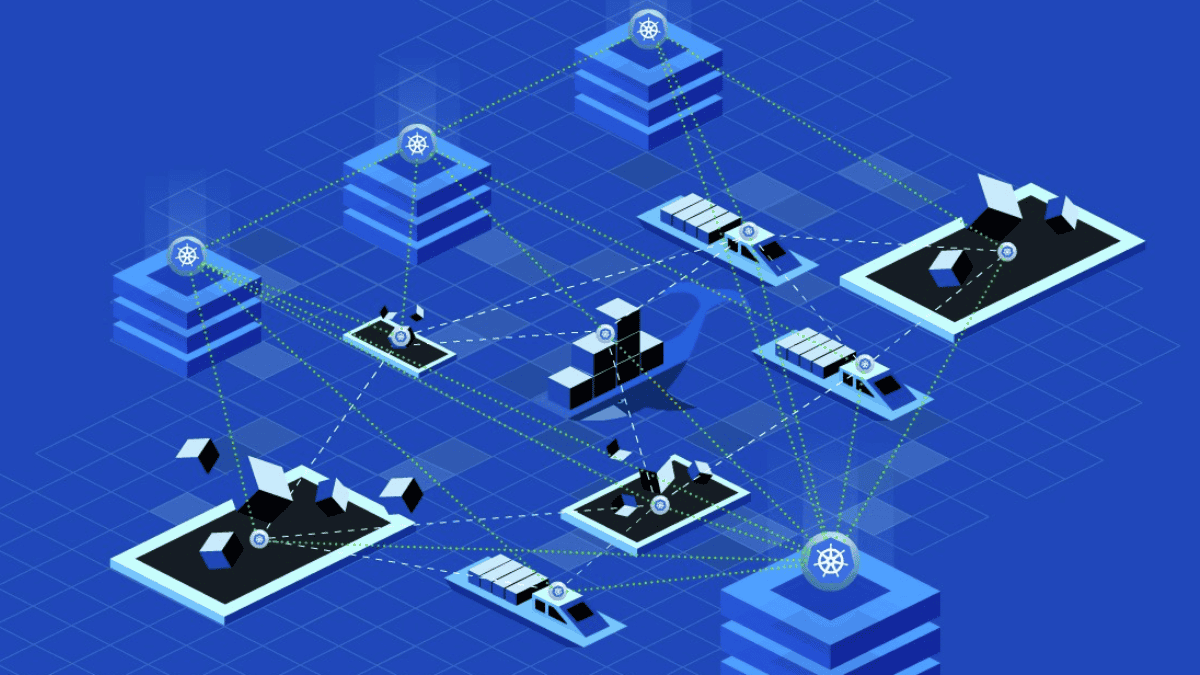
Kubernetes, often referred to as K8s, is an open-source container orchestration platform designed to automate the deployment, scaling, and management of containerized applications. Its primary […]

The landscape of cybersecurity threats is continuously evolving. Cybercriminals employ a variety of tactics to exploit vulnerabilities in systems, causing financial loss and disruption for […]

High availability refers to the systems and measures put in place to ensure that IT services are continuously operational and accessible. This concept involves minimizing […]