Insider threats emerge from individuals within an organization who exploit their access to sensitive data for malicious purposes or inadvertently cause harm. These individuals can […]

Vendor management is a crucial aspect of information technology (IT) that focuses on establishing and maintaining relationships with third-party service providers. For small and medium […]
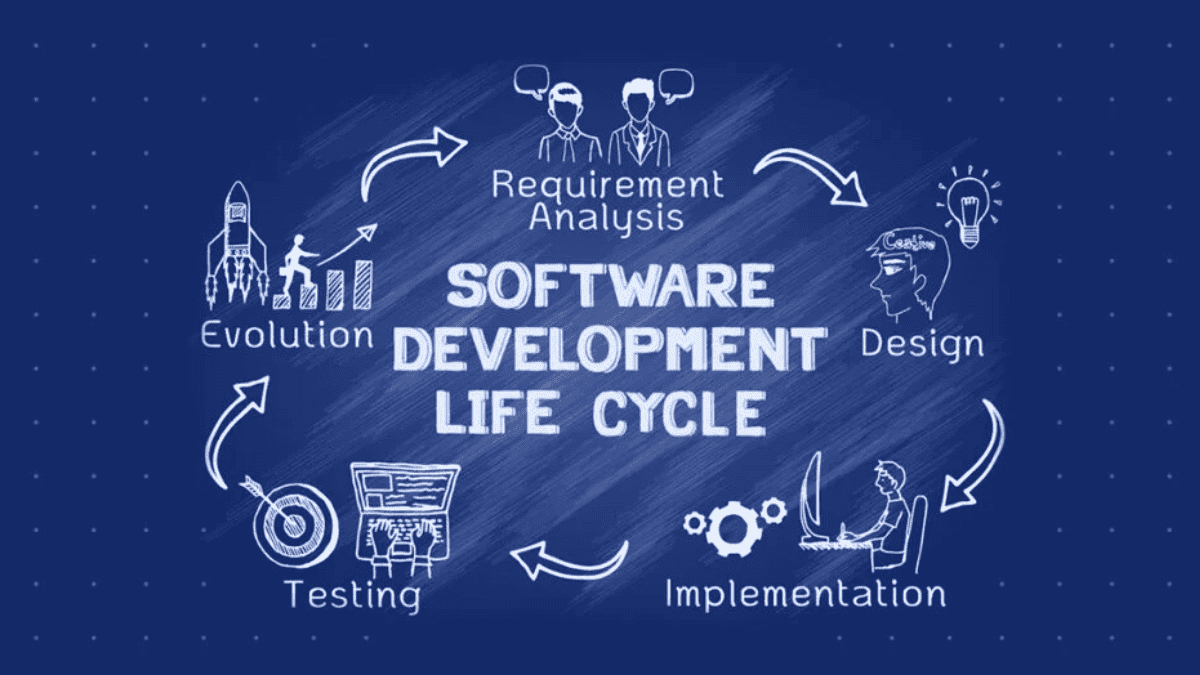
The Software Development Lifecycle (SDLC) is a structured process used by software developers and IT professionals to design, develop, test, and deploy software applications. This […]

In the modern digital landscape, small and medium-sized enterprises (SMEs) face a myriad of threats that can compromise their operations. Anti-malware tools are essential for […]
Machine learning is a subset of artificial intelligence that focuses on the development of algorithms that enable computers to learn from and make predictions based […]

Businesses face the unique challenge of balancing innovation with practical, day-to-day functionality. As you search for IT support in Cincinnati, it’s crucial to consider several […]

IT services are not just about fixing problems as they arise but about creating a technology environment that actively supports your business goals. A great […]

Network administrators play a crucial role in maintaining the integrity and functionality of an organization’s IT infrastructure. They serve as the backbone of a business's […]

Understanding what role switches play in network infrastructure is essential for small and medium enterprises (SMEs) looking to enhance their IT support capabilities. This section […]


