Phishing Attack Detection: The SLAM Technique for Small Businesses
Phishing is one of the biggest cybersecurity threats facing small businesses today. Criminals are constantly evolving their tactics, so companies must continuously improve their defenses against phishing attacks. Such threats directly take control of your personal information. This puts the future of your company at risk. Therefore, phishing attack detection is crucial.
This article explains the SLAM technique, an easy-to-remember strategy that empowers employees on how to detect phishing attacks.

Phishing Attack Detection Through SLAM Technique
What is a Phishing Attack, and Why is it Dangerous?
Phishing is a type of social engineering cyber attack that uses emails, texts, calls, and more to trick targets into handing over sensitive data or access. It often starts with a deceptive email designed to appear legitimate but coming from a scammer.
The studies conducted by security firms and industry groups have found that on average, businesses suffer a cost of $14 million per year due to phishing. The number of phishing attempts targeting small businesses in particular has risen sharply in recent years as criminals seek to exploit their often weaker defenses compared to large enterprises.
If you are wondering phishing is what type of attack, with just one click on a malicious link or file attachment in a phishing email, employees can expose your entire company's data and systems to cybercriminals. The consequences of a successful phishing attack can be severe, potentially leading to stolen customer information, hijacked accounts, ransomed data, fraudulent wire transfers, and more.
Recovering from a phishing breach can cost small businesses an average of $200,000 according to industry research. That's why ongoing phishing prevention training is crucial for all employees. Studies show phishing detection skills decrease by over 50% after just 6 months without reinforcement training.
How to Detect Phishing Attacks: The SLAM Technique
Now that you have understood what is a phishing attack, let’s look at how you can do it. SLAM is an easy-to-remember acronym to help employees quickly scan emails for red flags that indicate phishing attempts:
- Sender - Scrutinize the sender's email address and name
- Links - Look before you click any links in the email
- Attachments - Avoid opening strange, unexpected attachments
- Message - Read the message closely for odd requests or poor grammar
Using this simple, but effective, SLAM technique for small businesses takes just seconds to identify signs of phishing. Training employees to use SLAM can drastically improve your company's human firewall against phishing.
S - Scrutinize the Sender's Email Address
Carefully check that the sender's email address matches the company/person it claims to be from. Scammers often spoof legitimate addresses and names to impersonate trusted contacts or businesses.
- Search the full email address online to see if others have reported it as fraudulent. Scammers reuse addresses once they are flagged, so this can reveal ongoing phishing schemes.
- Check the full email header to look for spoofing techniques like slight misspellings or substitutions of letters/numbers that go unnoticed in the display name. Email headers contain the technical routing information and are where scammers often get sloppy with the actual address used.
- Verify any questionable emails by contacting the supposed sender directly on known good contact channels before responding. Don't reply to the suspect email itself.
L - Look Before You Click Any Links
Hover over any links in the email to preview the destination URL before clicking. Scammers use misleading URLs to send targets to fake login pages to harvest credentials or malware download pages. Even if your antivirus scans attachments, it doesn't scan links, which can lead to malicious sites. Don’t even accidentally click files that look suspicious.
On mobile devices, don't click any links at all in suspicious emails. Just delete them until you can properly inspect them on a desktop computer. Phishing links on mobile bypass many protections and land users directly in scammer traps.
A - Avoid Opening Strange Attachments
Never open unsolicited attachments in emails without scanning them first. Any file type such as Word, PDFs, or images can potentially contain malware now. Scammers disguise executable files as Office documents and more. An attachment may claim to be an invoice or receipt but contains a virus that can infect your system when opened.
Before enabling attachments in an email client, ensure antivirus is enabled and notifications for detected threats are on. If scanning does not flag an attachment as malicious, still exercise extreme caution before opening. Unexpected attachments from trusted contacts could mean their accounts have been compromised. When in doubt, verify attachments by contacting the sender directly before opening them.
M - Read the Message Closely
Read phishing emails fully and carefully before acting on any requests. Scammers count on targets, quickly skimming and missing obvious red flags in the message itself. Watch for:
- Poor spelling/grammar - Scammers are often foreign and make mistakes native speakers wouldn't.
- Odd or urgent requests - Pleas for quick action via money transfers, account updates, password resets, and more are common phishing tactics.
- Strange phrasing - Greetings like "Hello customer" or awkward wording also indicate phishing attempts.
- Unexpected logos/branding - Scammers often include fake company branding and logos to appear legitimate.
- Poor formatting - Text and images that don't align or broken hyperlinks demonstrate shoddy phishing emails.
Any of these signs, or just an overall "gut feeling" that an email seems off, warrant scrutiny before responding. Use the SLAM technique to inspect any questionable messages.
Protect Your Cincinnati Small Business Through Phishing Attack Detection
Defending against increasingly sophisticated phishing attacks requires expert help. LK Technologies, a leading Cincinnati-based IT company, offers customized phishing prevention training and cybersecurity solutions tailored for small to midsize businesses. Their security experts can:
- Audit your company's existing phishing vulnerabilities.
- Provide interactive phishing simulation training to employees. Generative AI tools can speed up phishing attacks by at least 40%, creating an even greater danger due to high scalability.
- Implement advanced email security and filtering tools to block phishing attempts. AI-powered programs now detect over 99% of phishing emails before they reach employees.
- Continuously monitor and defend against the latest phishing tactics and threats. New phishing techniques emerge daily as criminals innovate their attacks.
Protect your employees and data from phishing and other cyber threats - contact LK Technologies today for a free consultation on phishing attack detection! Investing in robust cybersecurity measures now can save your Cincinnati small business from potentially catastrophic data breaches down the road.
Example of Phishing Attacks detection:
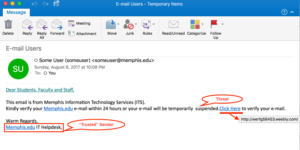
phishing_email_example
Example of a phishing email designed to look like it's from a legitimate company. Phishing emails often include logos and branding from trusted organizations and spoofed email addresses to appear authentic at first glance.


